How Browser Extensions Could Be Enabling Widespread Affiliate Commission Theft

As digital advertising revenue reached a record $258.6 billion in 2024 according to the IAB Internet Advertising Revenue Report, a darker side of the online ecosystem is coming to light. Browser extensions, those seemingly helpful tools that promise to protect privacy, block ads, or save consumers money, are increasingly being implicated in sophisticated schemes to steal affiliate commissions—potentially redirecting millions of dollars from legitimate businesses to fraudulent actors. The money saving extension Honey was recently caught overwriting affiliate cookies.
Recent security research has uncovered a network of browser extensions with over 6 million users that could be engaging in various forms of data collection and potentially commission theft, raising serious questions about extension security and the integrity of affiliate marketing programs.
The Discovery: A Network of Suspicious Extensions
A security researcher called John Tuckner recently investigated a list of browser extensions that an organization had configured for monitoring. What began as a routine evaluation led to the discovery of 57 suspicious extensions with nearly 6 million users collectively.
The investigation started with an “unlisted” extension in the Chrome Web Store called “Fire Shield Extension Protection,” which claimed to check other extensions for problematic permissions. Despite being unlisted—meaning it doesn’t appear in Chrome Web Store searches—this extension somehow accumulated 300,000 users.
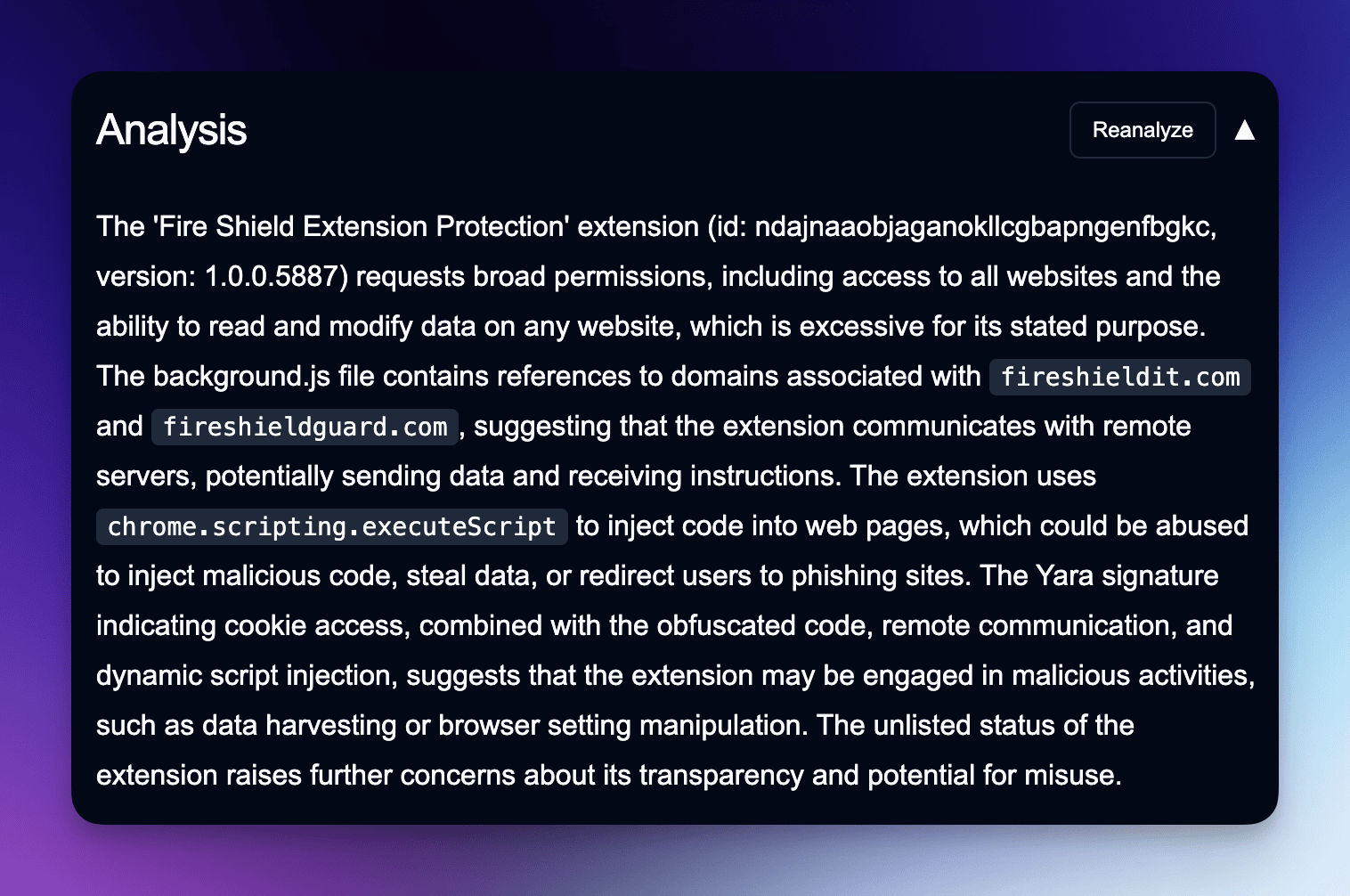
What raised immediate red flags was the extension’s extensive permission requests, including the ability to:
- Access web traffic on all URLs
- Access cookie storage
- Manage browser tabs
- Execute scripts on any website
Further analysis connected this extension to 34 others through a shared domain misspelled as “unknow.com” in their code. While the misspelled domain served no apparent purpose, it became a crucial fingerprint linking these extensions together.
The security researcher noted in their report that these extensions claim to perform purposes like ad blocking, extension protection, or privacy protection, but the code for their claimed purpose is often minimal or missing entirely.
The most concerning discovery was the extensions’ ability to be remotely controlled through configuration updates. By manipulating these settings, the extensions could potentially increase their level of user tracking and data collection.
Connection to Affiliate Commission Theft
While the browser extension research didn’t explicitly confirm commission theft, the capabilities of these extensions align perfectly with known methods of affiliate fraud. According to industry experts, affiliate commission theft has become increasingly sophisticated, often relying on tools that can manipulate browser behavior without users’ knowledge.
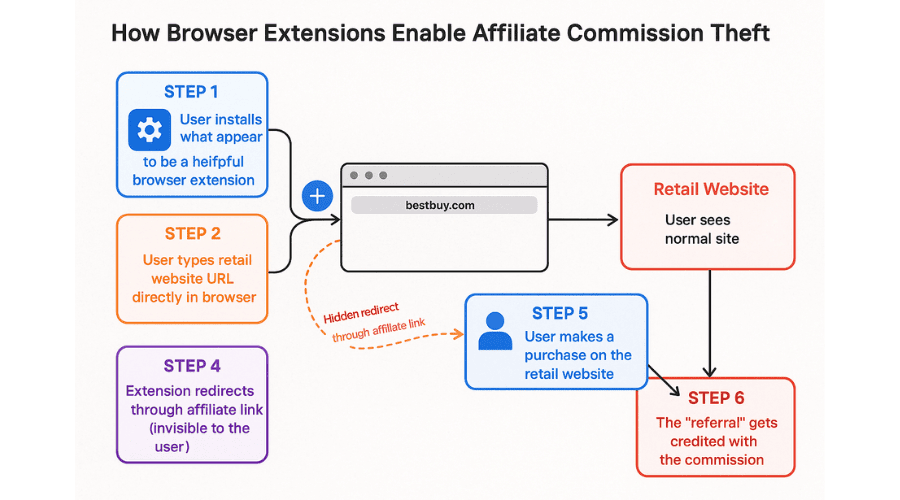
A Forbes article from as far back as 2013 on this topic explained how some browser extensions can silently redirect users through affiliate links even when they attempt to visit websites directly. The article described a demonstration where typing “bestbuy.com” into a browser with certain extensions installed briefly showed another URL appear and disappear—just long enough to drop a tracking cookie that would attribute any subsequent purchase to an affiliate.
The extensions discovered in the recent security research have numerous capabilities that could enable similar behavior:
- Functions to retrieve all cookies for any domain
- Setting long-standing tracking cookies
- Accessing sensitive headers like ‘Authorization’ and ‘Cookies’
- Ability to execute remote scripts on any webpage
- Capability to configure new search providers
One particularly concerning function found in the code allows the extensions to execute scripts retrieved from external URLs in an embedded iframe, potentially enabling interaction with any website the user is currently visiting.
The Scale of the Problem
The retail media network segment of digital advertising—which includes many affiliate programs—grew by 23% in 2024 to reach $53.7 billion, according to the IAB report. With this much money in play, affiliate fraud has become an increasingly attractive target for cybercriminals.
The extensions identified in the security research obtained their user base through methods that remain unclear, but evidence suggests they may have been distributed through malicious advertisements. Google Ad Transparency results show some of these extensions were likely delivered through ads, explaining how “unlisted” extensions could accumulate millions of users.
Bizarrely, some of these suspicious extensions were even marked as “Featured” in the Chrome Web Store despite being unlisted and unavailable through normal search, potentially misleading users into believing they were verified and reputable.
The Privacy Angle
The IAB report highlights how digital advertising is moving toward first-party data and privacy-compliant solutions in response to increased regulatory scrutiny and platform-level restrictions on tracking. In 2024, seven new states enacted comprehensive privacy laws, bringing the total to 20 active laws nationwide.
However, malicious browser extensions represent a significant blind spot in these privacy efforts. While legitimate advertisers adapt to a more privacy-conscious environment, these extensions potentially harvest user data without consent, operating outside the bounds of normal advertising channels.
The capability to access cookies, authorization headers, and other sensitive information gives these extensions potential access to far more personal data than even the most invasive legitimate advertising methods.
Who Benefits from Commission Theft?
According to the Forbes article on affiliate fraud, when affiliates steal sales using software that inserts their affiliate information even when users try to go directly to websites, it artificially inflates the revenue metrics used to measure the success of affiliate programs.
This creates a perverse incentive structure. Affiliate managers—whose performance is often measured by program revenue—may have little motivation to investigate suspicious activity if it appears to be driving sales.
“One of the major issues is the disincentive your affiliate managers have to find and correct these issues,” Adam Riemer stated in the Forbes article. “Since most affiliate managers are given better compensation or opportunity if their affiliate program is doing well, there is little reason for them to hunt down these quiet thieves.”
This aligns with the IAB report’s observation that advertisers are “now not only looking for where audiences are, but where commerce can happen,” making affiliate tracking manipulation an even more attractive target for fraudsters.
Types of Commission Theft
Browser extensions can facilitate several common types of commission theft:
Cookie Stuffing: The extensions can place affiliate tracking codes on a user’s computer without their knowledge, attributing future purchases to the fraudulent affiliate.
URL Hijacking: As demonstrated in the security research, extensions can redirect users through affiliate links even when they attempt to go directly to a website.
Click Fraud: The ability to execute scripts allows extensions to potentially generate fake clicks on affiliate links.
Intrusive Advertising: Extensions can manipulate the user’s browsing experience to generate fake clicks and conversions.
Misusing Brand Keywords: Extensions that manipulate search results can redirect traffic intended for brand searches through affiliate links.
The Business Impact
For companies with affiliate programs, this type of fraud has serious financial implications. When affiliates steal commissions through browser extensions, companies are essentially paying for sales they would have received anyway. This not only impacts profitability but also distorts marketing analytics and budget allocation.
“When I audit a program, I usually kick out 65-90% of the top performers,” Riemer stated in the Forbes article. “Although the affiliate program metrics decline, total sales stay the same and revenue goes higher because the company is not losing margin on commissions, coupons and network fees.“
The IAB report notes that digital advertising is increasingly focused on “channels that allow for incremental impact measurement.” However, affiliate fraud undermines this goal by falsely attributing organic traffic to fraudulent affiliates, making it impossible to accurately measure incremental impact.
The Way Forward
As the digital advertising industry continues to evolve, addressing the threat of malicious browser extensions and commission theft will require cooperation from multiple stakeholders:
Platform Providers: Google and other browser developers need to enhance their vetting process for extensions, particularly examining permission requests, code obfuscation, and remote control capabilities.
google has updated its policies since the Honey situation came to light:
- Inserting affiliate links when no discount, cashback, or donation is provided.
- An extension that continuously injects affiliate links in the background without related user action.
Advertisers and Merchants: Companies running affiliate programs should implement more sophisticated fraud detection systems and reconsider compensation structures for affiliate managers to incentivize fraud detection.
Security Researchers: Continued investigation and public disclosure of suspicious extensions, as seen in the recent research, remains crucial to raising awareness.
Regulatory Bodies: As privacy regulations expand nationwide, they should consider specific provisions addressing browser extension security and data collection practices.
The security researcher who uncovered the 57 suspicious extensions has submitted them to Google for review, but many remain active in the Chrome Web Store at the time of this report. Their investigation demonstrates that malicious browser extensions represent a significant and often overlooked threat in the digital advertising ecosystem—one that affects millions of users and potentially redirects millions of dollars in affiliate commissions.
As digital advertising and retail media networks continue their impressive growth, ensuring the integrity of these systems against increasingly sophisticated threats will be essential for maintaining trust in the digital economy.
Editor’s Note: This article was compiled from multiple research sources including the IAB Internet Advertising Revenue Report conducted by PwC, security research on browser extensions, and previous reporting on affiliate fraud. No specific companies beyond those explicitly named in the original sources have been identified as victims or perpetrators of the described activities, however the following companies are currently being investigated Honey (owned by PayPal), Rakuten, Capital One Shopping (formerly Wikibuy), Piggy, RetailMeNot, Ibotta, Cently, Drop, SlickDeals, CamelCamelCamel, Avast Safe Price, Coupert, Earny, BeFrugal, PriceBlink, Invisible Hand, Swagbucks, Coupon Cabin, Karma.






